April 14, 2025
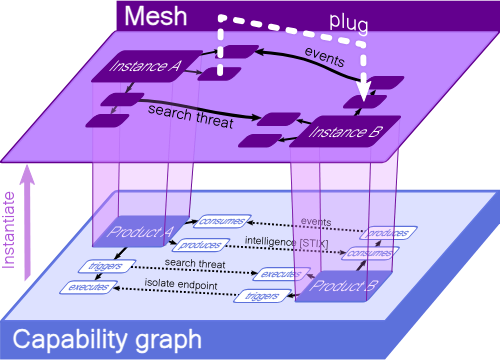
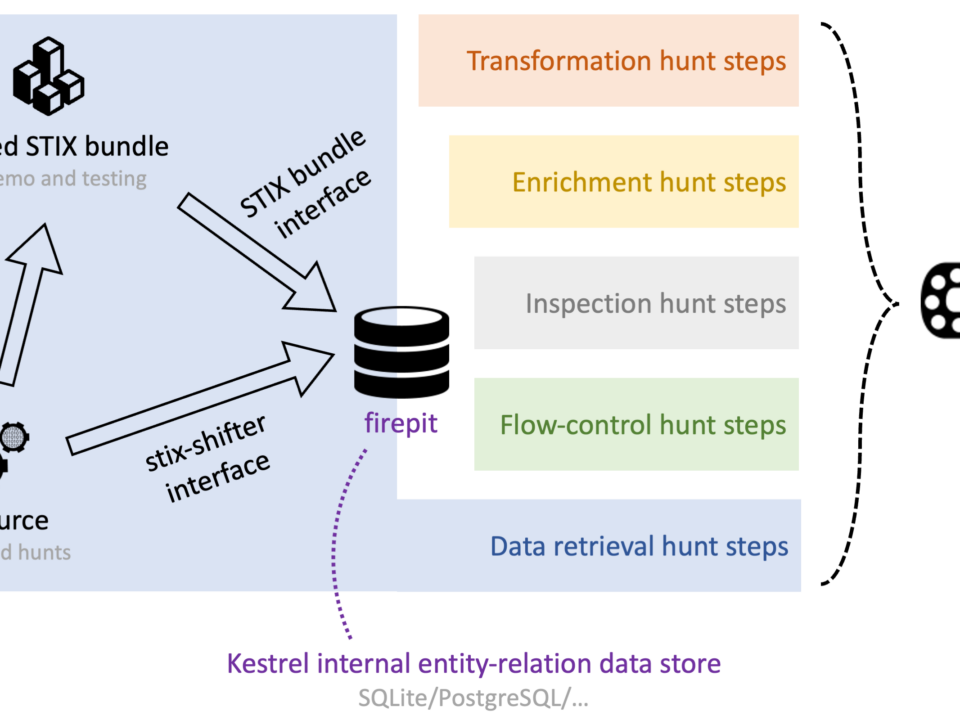
The cybersecurity industry faces a significant challenge: countless products need to integrate with each other to provide value to end users. This creates a massive, industry-wide integration problem due to the numerous integration requirements. Meshroom is a command-line tool to build and manage Cybersecurity Mesh Architectures (CSMA). It is part of the OXA sub-project under the Open Cybersecurity Alliance (OCA) and offers […]