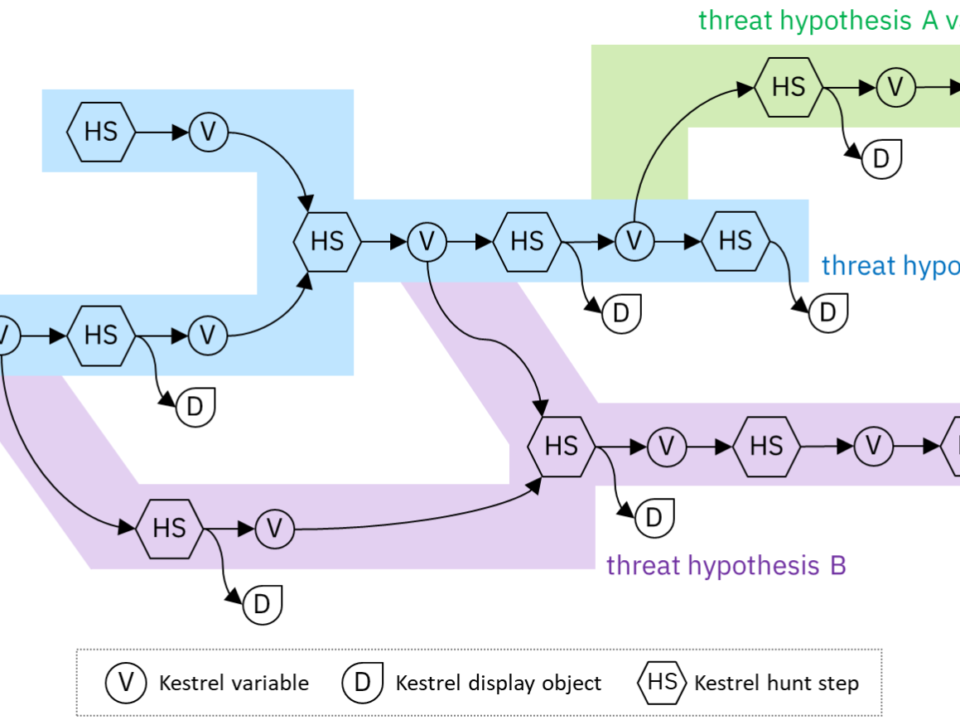
October 29, 2021
The security industry has evolved over the years to combat new and emerging cyber threats, and as we evolved, new products were launched to help security teams. Some of these products have been great breakthroughs – driven by the venture capital and innovation flowing to the security industry – but a lot of them have been a fad as they […]