Open Cybersecurity Alliance Event Drives Industry Collaboration During RSA 2022
June 20, 2022
Fun with securitydatasets.com and the Kestrel PowerShell Deobfuscator
October 31, 2022OCA is glad to introduce the Kestrel cloud sandbox. Now learning and trying Kestrel is just a click away—no installation needed, no server needed.
Taste And Learn Without Install?
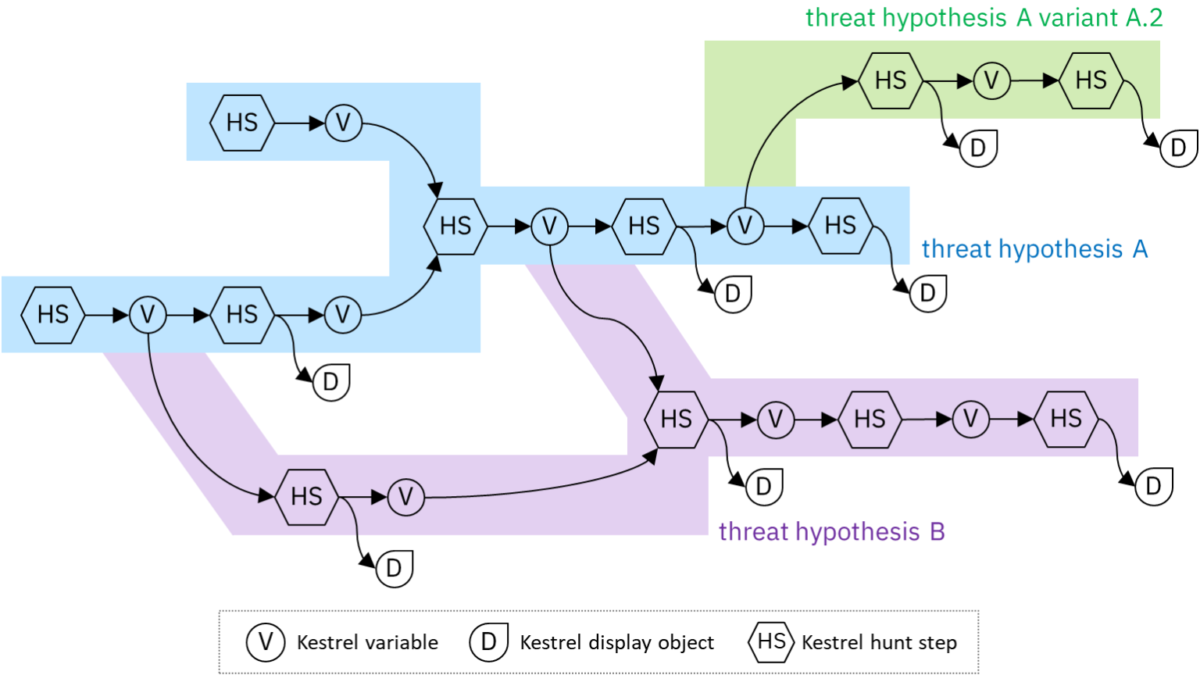
Kestrel is a novel approach to perform cyber threat hunting, letting threat hunters focus on the business (hunting) logic, other than query specification and adapter development. It constructs an entity-based cyber reasoning paradigm, which normalizes different data sources, and smooths out the procedure to compose hunt-flow from hunt steps.
Usually one needs to install Kestrel runtime before launching the first hello-world hunt. One may also clone the kestrel-analytics repo to use any community-shared analytics hunt steps. In addition, one may clone the kestrel-huntbook repo to download community-shared hunting playbooks and tutorials to start hunt and learn.
Could we have a sandbox pre-loaded with Kestrel runtime and all batteries? Then users can taste Kestrel and execute their hunts by spinning up an instance of the sandbox.
Launching a Kestrel Cloud Sandbox
Yes. The answer is the Kestrel cloud sandbox (built and managed by binder).
Kestrel team crafts two entrance URLs, either of which will spin up a Kestrel sandbox instance in a public cloud and open the tutorial or huntbooks directory in the kestrel-huntbook repo when entering the sandbox:
Take the first entrance URL as an example, after clicking it, binder will take a few seconds/minutes to prepare the sandbox. It may be slow when a new version is spun for the first time, which gets faster in follow-up runs.

The sandbox will then be launched, and the user will land to a classic Jupyter Notebook web interface (behind the scene, the sandbox is a container running in a public cloud partnered with binder). The sandbox has Jupyter, Kestrel runtime, Kestrel kernel, Kestrel analytics, and Kestrel huntbooks installed and setup, so the user is ready to explore and execute a huntbook in the sandbox.
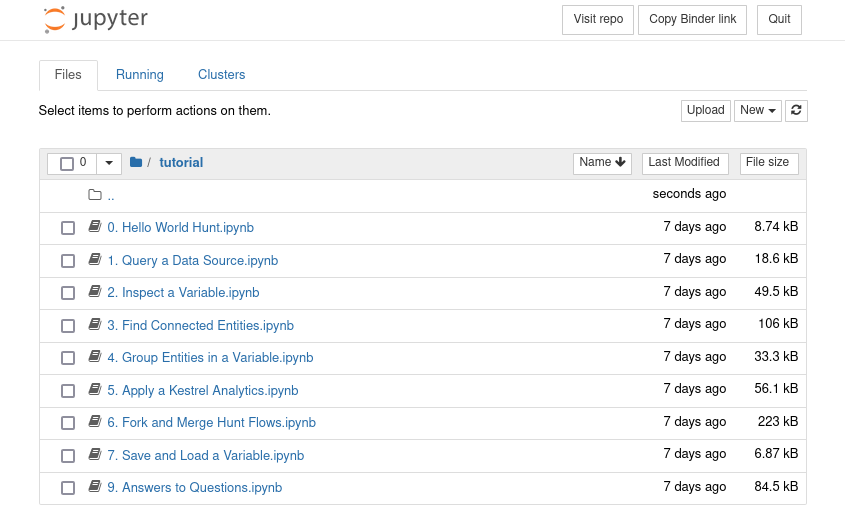
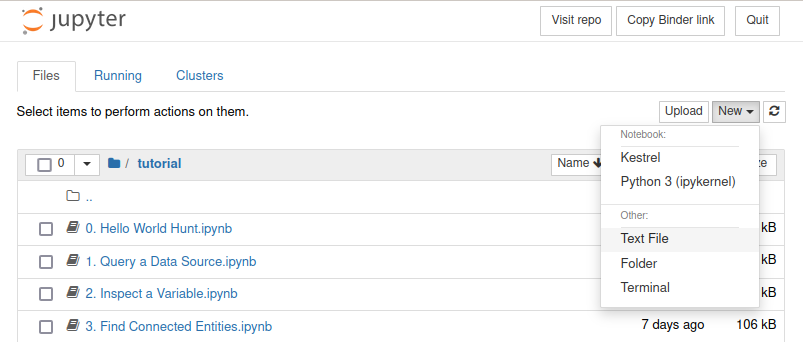
For instance, a user may click the huntbook 5. Apply a Kestrel Analytics.ipynb and open the huntbook with Kestrel Jupyter kernel. The huntbook is ready to view/edit/execute now.
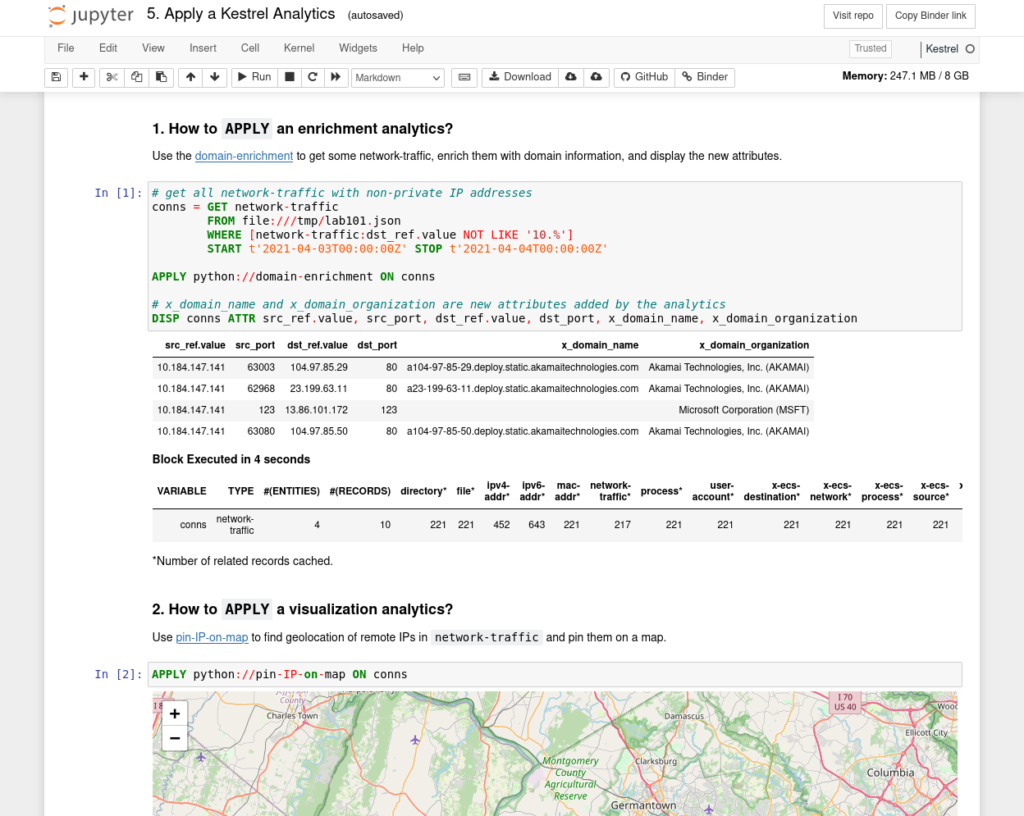
Connecting Your Data to Sandbox
People use the Kestrel sandbox to learn Kestrel, tweak existing huntbooks, play with them, and check the execution results. The hunts in the Kestrel tutorial use pre-canned data (STIX bundles) provided by the open-source Kestrel project.
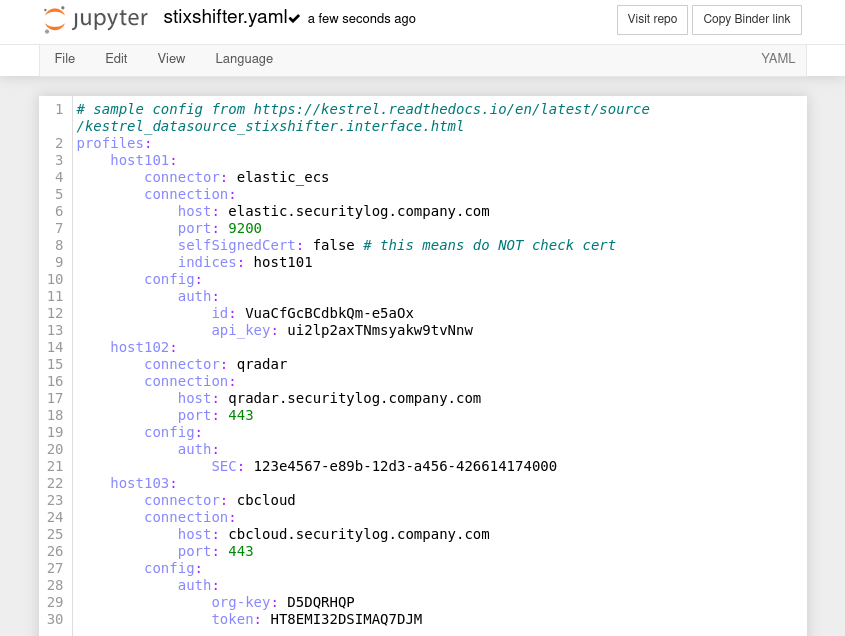
Beyond playing with the huntbooks, one could perform hunts directly in the sandbox. After launching a Kestrel sandbox, one can connect their own data sources by creating a stix-shifter interface config file named stixshifter.yaml using the text editor.
Now any huntbook in the same directory of the stixshifter.yaml file will be able to use data sources defined in the stixshifter.yaml.
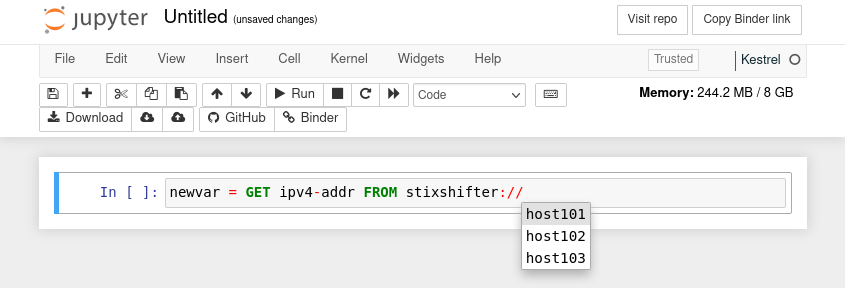
To start a hunt, click the New button on the top right and choose Kestrel as the notebook kernel. Write in the notebook newvar = GET ipv4-addr FROM stixshifter:// and press tab to list (auto-complete) all data sources in the stixshifter.yaml file.
Note that (i) bringing data to a public sandbox will expose the data during transmitting and storing, and (ii) utilizing public cloud for hunting is subject to the terms of use of the public cloud partnered with binder. Check the kestrel-huntbook repo README to understand the terms from different parties/providers before hunt in public sandboxes.
Hunting in Your Own Environments
After playing with Kestrel in the sandbox, it is recommended to conduct your own hunt in your own environment. This means to install Kestrel on your hunting workstation/laptop, or in a server for cyber threat hunting. Because Kestrel can be accessed as a Jupyter Notebook, the only requirements for a place to install Kestrel are:
- it has access to data sources
- it can be accessed from the hunter’s workstation/laptop
After deciding where to host Kestrel runtime, one can follow Kestrel doc to install/setup:
The installation is simple—just pip install—In the future, we may provide pre-built Kestrel container for people to pull and execute even simpler.
Until next time, happy threat hunting! And don’t forget to create a PR to kestrel-huntbook to share your huntbooks with the community.
Dr. Xiaokui Shu is a Senior Research Scientist at IBM Research and the Technical Steering Committee Chair of the Open Cybersecurity Alliance (OCA).