Setting Up The Open Hunting Stack in Hybrid Cloud With Kestrel and SysFlow
November 2, 2021
Events with OCA participation in April, May and June
March 24, 2022Most security teams use several security tools to manage the security infrastructure within their organization. Each tool was acquired to solve a specific problem. Each tool added to the environment poses a different challenge. Almost 50% of newly acquired security tools require individually coded integrations. How bad is it? Most large security teams are equally represented by analysts and integrators. It takes a lot of time and effort to implement a tool properly. Along with installation, testing, tuning, patching, and compliance, the tool needs to be incorporated into your environment and processes. Ideally, you would also train your team to use the new tool. These activities take time and attention away from security tasks and can significantly reduce your team’s effectiveness.
“Analysts like Forrester and 451 Research have reported on security tool sprawl in the past few years, noting that as many as 40% of organizations admit that their development teams are so overwhelmed by security alerts that they can’t respond to at least 25% of them.”
Then, there is the issue of the increasing numbers of security products or tool sprawl, which adds to security complexity. While tool unmanageability doesn’t happen overnight, it slowly creeps in with every addition of a new solution. Gathering information across multiple tools and disparate data sources takes time, and time is a precious commodity especially in your SOC where seconds matter. Instead of fixing a problem, businesses suddenly have added orchestration complications. Tool proliferation is a well-documented concern. Analysts like Forrester and 451 Research have reported on security tool sprawl in the past few years, noting that as many as 40% of organizations admit that their development teams are so overwhelmed by security alerts that they can’t respond to at least 25% of them. The main repercussions that businesses will experience with multiple point solutions is excessive costs and less effective threat responses.
This is a two-pronged issue. Not only is tool integration demanding, but tool proliferation also exacerbates the problem. Most often, the security teams have functioned as the human glue to stitch disparate tools together. The security ecosystem of today needs to look at better ways to work together and to stop working in silos. The Open Cybersecurity Alliance was formed to supply answers to these vexing obstacles.
Open Cybersecurity Alliance
The Open Cybersecurity Alliance (OCA) is an open-source community with the mission of increasing interoperability across the security industry by developing and promoting sets of common code, tooling, patterns, and practices so that cybersecurity tools can share data.
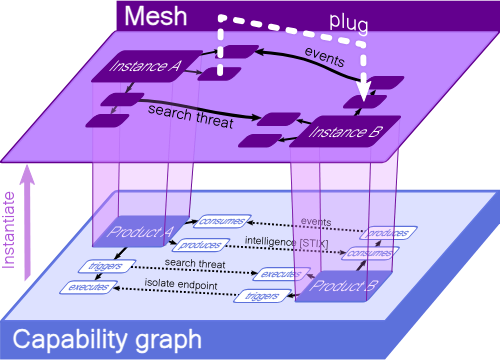
The OCA, formed under the auspices of OASIS Open, aims to foster collaboration between vendors, public and private organizations and security practitioners to drive security interoperability. Open Cybersecurity Alliance is building an open ecosystem where cybersecurity products interoperate without the need for customized integrations. Using community-developed standards and practices, OCA is simplifying integration across the threat lifecycle. In a recent blog on top technology trends, Gartner refers to a cybersecurity mesh architecture, which aligns closely with the work underway in OCA.
This open collaboration has the potential to greatly improve the AS-IS ecosystem with products that can seamlessly interoperate with one another. This would reduce the time it takes to integrate new tools. Creating an opportunity for security teams to be more efficient, businesses to get more Return on Investment (ROI) on tools they already have, and the opportunity for improved products, features, and services – helping drive the outcome of an even stronger security posture.
Current OCA Projects
Open Cybersecurity Alliance is building an open ecosystem where cybersecurity products interoperate without the need for customized integrations. Using community-developed standards and practices, OCA is simplifying integration across the threat lifecycle.
Some of the community’s most recent projects can be seen in the following graphic.

Who Should Get Involved?
Developers and cyber specialists from the public and private sector, corporate supporters, and technology consumers all have a voice in shaping the future of security and driving interoperability between security tools.
How You Benefit from Joining the OCA
Simply put, you will reduce costs by reducing the complexity of architecting and deploying ever-increasing cyber solutions.
Unlike industry-specific platforms for sharing threat data, OCA is uniquely focused on product interoperability, with benefits for the entire cybersecurity community. Unlike vendor partner alliances, OCA is a collaborative community with open governance. OCA is working on projects that span key conversations happening in the security industry, including, Zero Trust, Extended Detection and Response (XDR), and more.
As Jon Olstik recently pointed out in his blog for CSO, ‘Openness is Critical!’. Look at the OCA projects that interest you, get involved. We need your help to change/create the data formats, and standards we all will leverage to improve the Security Ecosystem.

How to Get Involved
- Join us on Slack
- Join the various project and discussion lists:
https://lists.oasis-open-projects.org/g/oca
For more information on sponsorship opportunities, contact Dee Schur, dee.schur@oasis-open.org