OCA and Kestrel at Black Hat 2023
August 8, 2023
Cybersecurity Automation Village
February 2, 2024Kestrel as a Service
The Open Cybersecurity Alliance (OCA) is excited to announce the next milestone of the Kestrel subproject, Kestrel as a Service (KaaS). KaaS enables threat hunting at scale to improve threat detection. It is a Kestrel container and a deployable cloud-managed hunting service for large organizations. The project provides the code and instructions for deploying a Threat Hunting Team Enterprise Solution that is focused on being scalable, persistent and collaborative. In this blog we will touch on some key concepts to initially describe our efforts and we will publish more in the future, for example, the KaaS getting started guide.
Team Threat Hunting
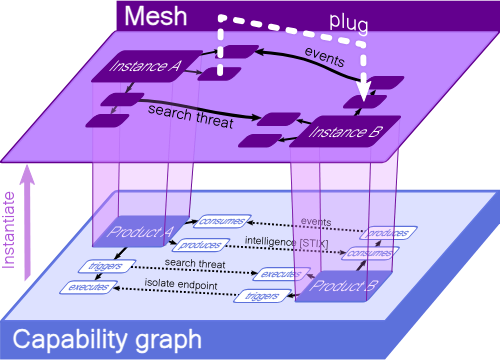
As described in the kestrel language documentation, hunters answer both questions of what to hunt and how to hunt. Kestrel is comprised of a language for humans to express what to hunt and a machine interpreter that deals with how to hunt. Kestrel is an OCA open source project that provides assistance for threat hunters for both concepts. Human intelligence and creativity are the irreplaceable secret sauce of asking and answering the questions of the what. The how is a translation between the knowledge in what and the execution instructions specified by different hunting platforms. Kestrel provides a layer of abstraction to stop the repetition involved in cyberthreat hunting.
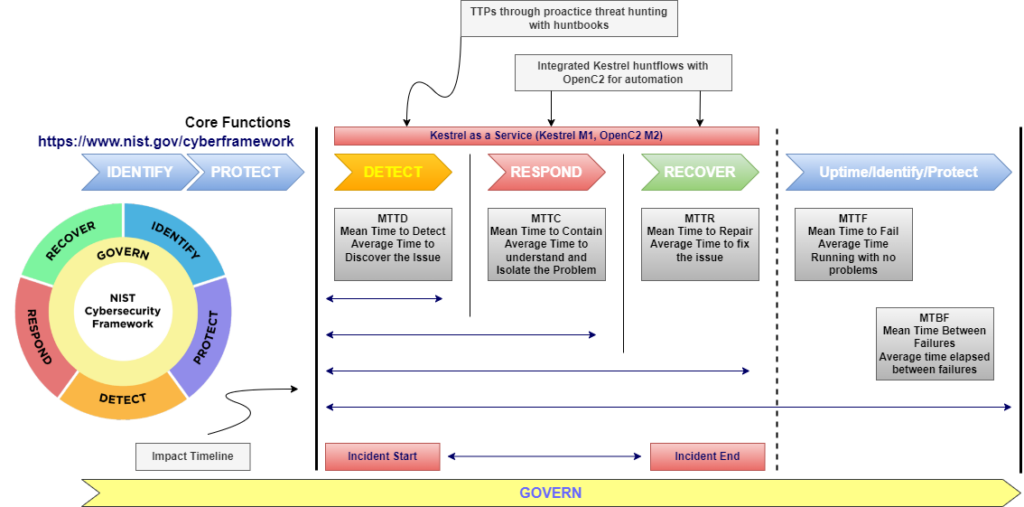
As indicated, threat hunting can be slow and tedious due to the manual steps required for answering a hypothesis and what to hunt. Although Kestrel improves the time to detect, there are limitations to team capabilities and metrics in threat hunting tools and standards. The power of team threat hunting is the ability to remove or minimize the limitations, therefore, decreasing the Mean Time to Detect (MTTD) or Dwell Time. This is achieved by combining a container platform, Authentication, Authorization, Kestrel, JupyterHub, and Kestrel hunt books. These combined components help improve security posture, provide persistence capabilities, and provide collaboration for the project team members.
Timeline Analysis
The first step in threat hunting is the hypothesis or statement that defines the hunter’s thoughts on what threats might be in the environment and how to find them. The remaining steps are – collection and processing of data, triggers, investigation and response. The goal of the KaaS project is to take these processes and not just have a successful hunt but to make the times of impact shorter through the team hunt service. In the diagram below, the NIST Cybersecurity Framework (CSF) detect function is our target metric to use for tracking improvements of a team using the service. We want to compare this against a single threat hunter with no collaboration and persistence. The detect function in NIST CSF is defined as “Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event”. We will also be analyzing respond and recover with Kestrel and OpenC2 in KaaS.
Join our effort
We want you to help us to build a threat hunting service community. Membership is free and open to the public. We hope you’ll join us in the KaaS Project. Keep on the lookout for announcements on more blogs, features and improvements.
Learn more about KaaS
If you want to learn even more about KaaS and the OCA sub-project, then jump over to the KaaS Project on Github or on the KaaS Slack Chat:
- Say hello in the Slack #introductions channel and then check out the #kestrel-as-a-service channel
- Check out the OCA Github KaaS Repository for code, documentation and more.
About the Open Cybersecurity Alliance
The Open Cybersecurity Alliance brings together vendors and end-users to create an open cybersecurity ecosystem where products can freely exchange information, insights, analytics, and orchestrated response. OCA supports commonly developed code and tooling and the use of mutually agreed upon technologies, data standards, and procedures. The OCA is governed under the auspices of OASIS Open, which offers projects a path to standardization and de jure approval for reference in international policy and procurement.
The OCA is led by these organizations committed to solving the costly problem of siloed cyber tools and products: Canadian Institute for Cybersecurity, Center for Internet Security (CIS), Cydarm, Cyware, EclecticIQ, IBM Security, Prophecy International, Rapid7, SAIC, sFractal Consulting, and VMware.
Media inquiries
communications@oasis-open.org