October 30, 2021
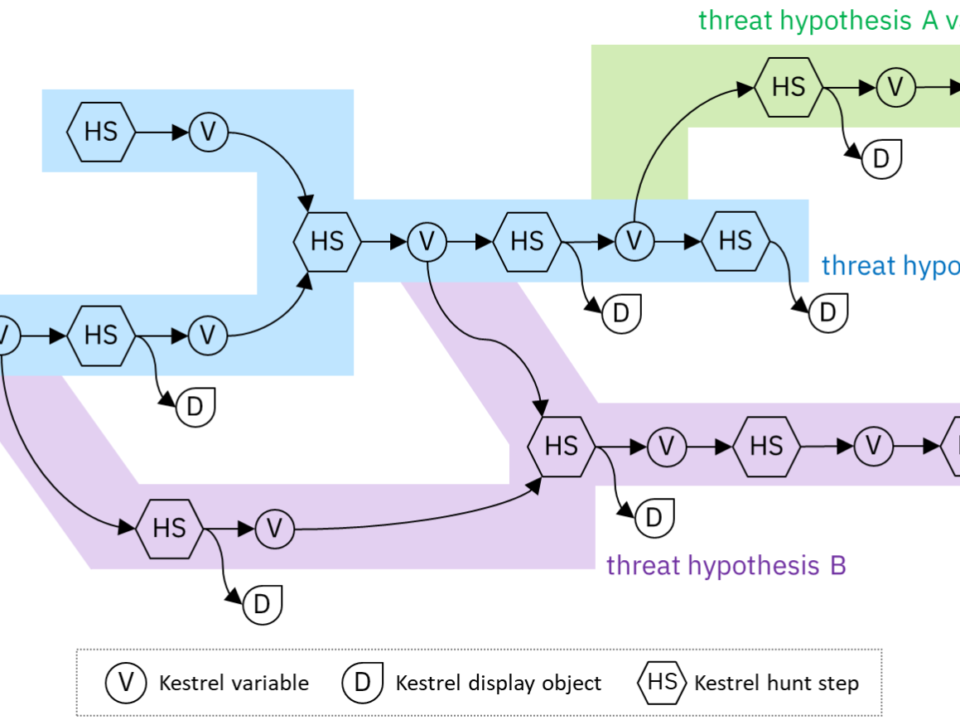
The seemingly endless stream of supply chain exploitation and ransomware disruptions have made it painfully clear that malware is already inside the perimeter, and has been there – undetected – for some time. With mounting pressure to address this issue, a significant number of regulatory and standards efforts have begun to consider Zero Trust as part of the answer. With […]